For decades, the username and password combination has been the core method by which owners and administrators authenticate users. There’s just one problem: passwords are terrible. The username-plus-password system is remarkably flawed, simultaneously frustrating and challenging for users to manage, and relatively easy for bad actors to penetrate.
Enterprise businesses have been using earlier forms of two-factor authentication (2FA) and multifactor authentication (MFA) for decades. But the cost and complexity of these systems had long been hurdles for smaller businesses.
In the last decade or so, 2FA has grown in prominence and is now a standard offering for many if not most sensitive consumer accounts. It’s a significant step toward better security: adding a second layer of authentication (whether it’s just a text message or a phone call) makes an attacker’s job more difficult by several orders of magnitude.
Still, that pesky password remains a part of the equation in many consumer-facing 2FA applications. And passwords remain comparatively weak in terms of absolute security.
Now, with passwordless authentication platforms, it’s finally time for passwords to go away — especially for the most critical security scenarios.
In this guide, you’ll learn:
- What passwordless authentication platforms are, and what they do
- Why companies implement passwordless authentication platforms
- How passwordless authentication platforms work (high-level overview)
- Pros and cons of passwordless authentication platforms
- Top vendors providing passwordless authentication platforms
Let’s get started with a definition of the term.
What Are Passwordless Authentication Platforms? A Definition
Passwordless authentication systems provide multifactor authentication in which a traditional username and password combination is not one of the factors. With passwordless authentication, users don’t use an alphanumeric password (one that they have chosen and memorized) at all.
Most passwordless authentication systems rely on a combination of something a user has and something a user is. Items in the first category could include a trusted mobile device, an app-based security key on that device, or even a separate hardware security key. Items in the second tend to be biometric.
Some newer solutions may increase security but fail to reach the standards of a passwordless authentication platform. For example, true passwordless authentication systems don’t rely on SMS-based codes. In addition, password managers that lock away a trove of passwords within a “secure vault” protected by a master password don’t qualify, either.
Why Should Companies Consider Passwordless Authentication Platforms?
The simple answer is that passwords are weak and easily compromised. Users hear that they should use unique passwords for every account or service they use, but remembering ten different complex passwords — much less 100 — is more than most people can do.
So, in response, they do all sorts of things that security professionals tell them not to do. They reuse passwords across dozens of sites so that if one account gets breached, all become vulnerable. They write down username and password combinations on sticky notes that they leave in plain view of anyone who walks by their workstations.
Your employees also share personal logins (Netflix, for example) with people they think they can trust, but then they use the same no-longer-secure credentials for sensitive business accounts.
People also get fooled into handing out business-related credentials through phishing schemes and spear-phishing attacks.
To sum up: if the only thing protecting your company’s most sensitive data is a username and password combination, the question is when — not if — a bad actor will gain access.
Besides passwordless, other multifactor solutions exist, and many of those will significantly increase security over a simple username and password combination. But many of these use proprietary systems that don’t always integrate well with complex business environments.
Standards-based passwordless authentication software is arguably the best method currently available for authenticating business systems. It strikes a reasonable balance, offering both strong security and relative ease of access for credentialed personnel.
The combination of both a physical token (something that the user must currently have possession of) and a physical attribute (which, except under the most violent of circumstances, the user will also possess) is exceptionally complicated to bypass or penetrate. In a typical passwordless authentication system, a bad actor would have to simultaneously do two things to infiltrate the system:
- Gain physical access to a credentialed user’s secure mobile device or hardware key.
- Steal or forge the right piece of biometric data.
While doing so is not entirely impossible, it is exceptionally infrequent in the real world.
How Do Passwordless Authentication Platforms Work?
At a high-level overview, the way passwordless authentication systems work is pretty simple. The system looks for two (or sometimes more) separate factors of authentication. If a user has them, the user gains access to the secured system. If not, then the user doesn’t gain access.
There may be secondary mechanisms in place similar to the “Forgot password?” button on every retail site login screen. But where these exist, they aren’t as simple as generating a link to an email address. Backup methods may include voice authentication, SMS-based authentication, or even email authentications. Businesses can choose which backup methods, if any, to allow.
Of course, the behind-the-scenes mechanics of how exactly these authentication platforms match factors with users in a secure way are deeply complex, far outside the scope of what a typical user needs to understand.
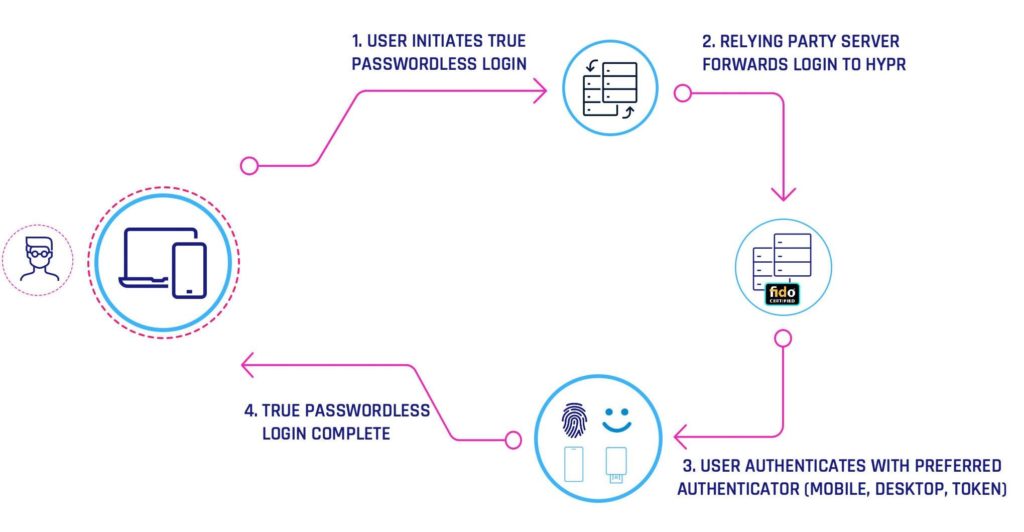
Each solution operates in a slightly different way, but here’s a flowchart showing how one provider explains their process:
Features, Functions, and Capabilities of Passwordless Authentication Platforms
There is some variety in terms of exactly which features and functions each passwordless authentication service offers. But to qualify for the category, a solution needs to do the following:
- Require non-password authentication to log in
- Use a Fast ID Online (FIDO)-compliant tool for that authentication (typically an authenticator app or physical security key)
- Offer or require multiple types or layers of authentication
Beyond those minimum features, passwordless authentication systems may also include features, functions, and capabilities like these:
- Factor sequencing
- Device Trust
- Passwordless customer authentication
- Desktop single sign-on
- Remote login
Pros and Cons of Passwordless Authentication Platforms
Before implementing a passwordless authentication system for your business, consider these advantages and drawbacks.
Pro: Stronger Authentication That’s Much Harder to Steal
Using a passwordless authentication system instantly catapults your account security to a much higher level. No solution eliminates 100% of threats, but threat actors will have a substantially more challenging task if they attempt to gain access by stolen credentials. You’ll undoubtedly protect yourself against attacks of opportunity, where bad actors simply try long lists of stolen credentials.
Pro: No Passwords to Guess
The stats on poor password use are atrocious. One security research firm identified 2.5 million users who chose “123456” as their password, and their other conclusions are just as shocking. Even more elegant passwords can still be easy to brute-force, and bad actors don’t even need very sophisticated tools to do so. But with passwordless, there are no passwords to guess or brute-force.
Con: Increased Difficulty of Use
As bad as the password system is, at least people understand it. Passwordless is still a little fuzzy for many, so your tech-averse employees may have difficulty adapting to it. There’s also the hassle of always needing one or two forms of authentication on your person.
Con: Lockouts and Lost/Forgotten/Stolen Devices
As with any new system, there’s a learning curve. Employees will inevitably lose a phone or physical hardware key, creating new threats, not to mention lost work time while a user works to regain access.
Top Vendors Providing Passwordless Authentication Platforms
Below are the most notable providers of passwordless authentication systems. Among these options, you should have no trouble finding a solution that meets your business’s needs.